Picking the Right Google Workspace Subscription for Your Business
 To meet widely varying customer needs, Google offers five core subscription options spread over two tiers. For larger organizations with frontline and deskless information workers, Google offers additional, specialized license options. If you are looking at a Google Workspace subscription for the first time, considering an upgrade, or looking for Gemini AI features, you’ll want to choose the subscription and licensing that meets your needs without overpaying.
To meet widely varying customer needs, Google offers five core subscription options spread over two tiers. For larger organizations with frontline and deskless information workers, Google offers additional, specialized license options. If you are looking at a Google Workspace subscription for the first time, considering an upgrade, or looking for Gemini AI features, you’ll want to choose the subscription and licensing that meets your needs without overpaying.
Subscription Tiers
Business Tier
Businesses with fewer than 300 employees typically select one of the Business Tier subscriptions– Workspace Starter, Standard, and Plus. These subscriptions limit the number of users and focus on the features and security most appropriate for smaller organizations.
Enterprise Tier
Larger businesses, as well as those requiring more advanced capabilities and security, often opt for the Enterprise Tier subscriptions– Standard and Plus. The Enterprise Tier also includes specialized license versions for frontline workers and knowledge workers with other email services.
Selection Criteria
When selecting a subscription, most businesses focus on a few key capabilities, such as:
- Storage capacity and shared drives
- Vault archiving/e-discovery
- Google Meet features
- Select security capabilities
With AI now integrated into all Google Workspace subscriptions, you should take time to understand the Gemini features included in each plan. A deeper review of security features can also help guide your selection.
Here is a deeper look at key selection criteria.
Storage
Since September 2024, all Google Workspace subscriptions use pooled storage.
Vault, the compliant archive/e-discovery service, covers Gmail, Drive, Groups, Chat, and Calendar, is available for all Enterprise Tier subscriptions and Business Plus.
The amount of storage, allocated per user and pooled, is as follows:
Business Tier
- Starter = 30 GB
- Standard = 2 TB
- Plus = 5 TB
Enterprise Tier
- Essentials = 1 TB
- Standard = 5 TB
- Plus = 5 TB
Meet
Google Meet is a robust meeting and collaboration system that generally negates the need for third party solutions.
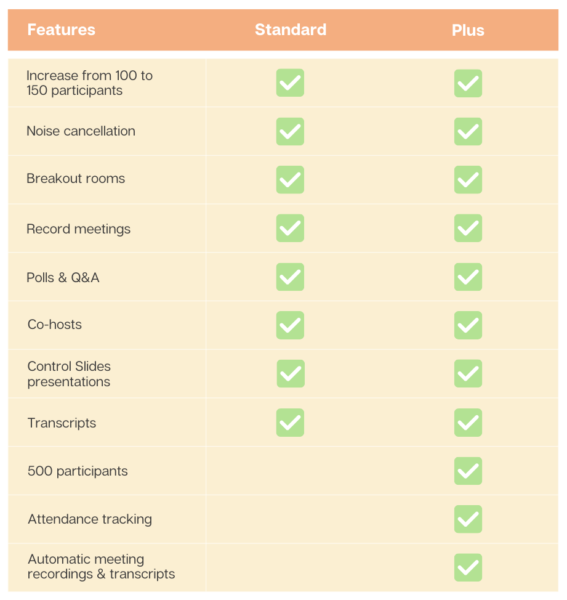
Meet Features in Business Standard and Plus Subscriptions
All Google Workspace licenses include a core set of features:
- External participants
- Secure meetings
- Screen sharing
- Mobile app
- Dial-in (US & international)
- Digital whiteboard
- Hand raising
- Reaction
At the Business Tier, Meet features scale up as noted in the table.
The Enterprise Tier includes live streaming and additional security features with all licensees.
Participant limits increment as follows:
- Essentials: 250
- Standard: 500
- Plus: 1000
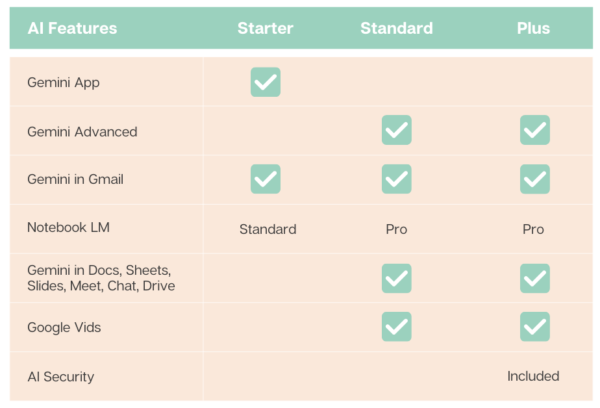
Gemini AI in Google Workspace
The following matrix summarizes the Gemini AI features in each of the core Google Workspace subscriptions.
Security
Google Workspace provides a comprehensive set of security features and tools. With too many settings and options to list here, we published a Google Workspace Security Feature Matrix as an eBook.
Review security features against your regulatory, industry, and business requirements.
Selection Process
When evaluating Google Workspace subscriptions, it’s essential to assess the details. Part of your selection process should include determining whether selecting a higher subscription tier or upgrading is more cost-effective than integrating third-party tools to provide the functionality you need.
For example, while Google Workspace’s Standard Data Protection includes email sandboxing, the feature does not offer the same capabilities– such as QR code analysis– as many third-party email threat protection services.
In many cases, upgrading your Google Workspace subscription provides the needed capabilities at a lower cost than using a third-party tool. This is often true for Google Meet compared to third-party web meeting tools like Zoom.
For other capabilities, however, a third-party integrated solution may still be required.
Your Next Steps
For help assessing your needs and options, please contact us or schedule a brief intro call with a Cloud Advisor.
About the Author
 Bill is a Senior Cloud Advisor responsible for helping small and midsize organizations with cloud forward solutions that meet their business needs, priorities, and budgets. Bill works with executives, leaders, and team members to understand workflows, identify strategic goals and tactical requirements, and design solutions and implementation phases. Having helped over 200 organizations successfully adopt cloud solutions, his expertise and working style ensure a comfortable experience effective change management.
Bill is a Senior Cloud Advisor responsible for helping small and midsize organizations with cloud forward solutions that meet their business needs, priorities, and budgets. Bill works with executives, leaders, and team members to understand workflows, identify strategic goals and tactical requirements, and design solutions and implementation phases. Having helped over 200 organizations successfully adopt cloud solutions, his expertise and working style ensure a comfortable experience effective change management.

 In today’s fast-paced business world, the ability to maintain continuous PC operations is crucial for your business. With limited resources and manpower, you cannot afford to lose data or prolonged downtime.
In today’s fast-paced business world, the ability to maintain continuous PC operations is crucial for your business. With limited resources and manpower, you cannot afford to lose data or prolonged downtime. 
 Cyber threats are evolving at an alarming rate, posing significant risks to your business. Penetration testing, commonly referred to as “pen testing,” is becoming a vital, proactive tool for assessing your risks.
Cyber threats are evolving at an alarming rate, posing significant risks to your business. Penetration testing, commonly referred to as “pen testing,” is becoming a vital, proactive tool for assessing your risks. Cyber Security Will Change Companies
Cyber Security Will Change Companies