Google Workspace: Gemini AI Features and Pricing Changes
Updated January 22, 2025, at 2:00 pm et: See the easier to read chart and text that is in bold italics.
 On January 15, 2025, Google announced a major shift for Google Workspace. Going forward, all Google Workspace licenses will include Gemini AI features and functions. Specific capabilities will vary by license type.
On January 15, 2025, Google announced a major shift for Google Workspace. Going forward, all Google Workspace licenses will include Gemini AI features and functions. Specific capabilities will vary by license type.
While customers will no longer need to pay as much as $30 per user per month for these capabilities, the cost for most Google Workspace subscriptions will increase by about 17%. This increase affects all subscriptions, even those opting not to use the newly embedded Gemini AI features.
For new customers purchasing directly from Google, the price increase took effect immediately.
For existing customers, Cumulus Global customers, and those working with other Google partners, the price increase takes effect on March 17, 2025.
- If you have a Flexible Plan subscription, you will see the increase as of March 17, 2025.
- If you have an Annual Plan subscription, or a multi-year agreement, you will see the increase at their next subscription renewal. You will not be charged for the additional Gemini AI functionality until this renewal (see below).
Product Update Highlights:
The product highlights, and caveats are as follows:
- The Gemini App (gemini.google.com) remains
- Gemini for Google Workspace is replaced by the embedded features based on your subscription.
- All versions of Google Workspace will now include Gemini AI features.
- Google is deploying the Gemini AI features to existing customers in phases between January and March, 2026
- The Gemini AI features will be enabled, by default, for all users
- Enterprise Tier subscriptions can manage and disable Gemini AI features
- Business Tier subscriptions must request access to Gemini AI admin controls
Pricing and AI Features Matrix
The following table summarizes the price increases and Gemini AI features for both the Google Workspace Business and Enterprise tiers with Annual Plan Pricing. Flexible Plan prices increase similarly, reflecting a 20% upcharge.
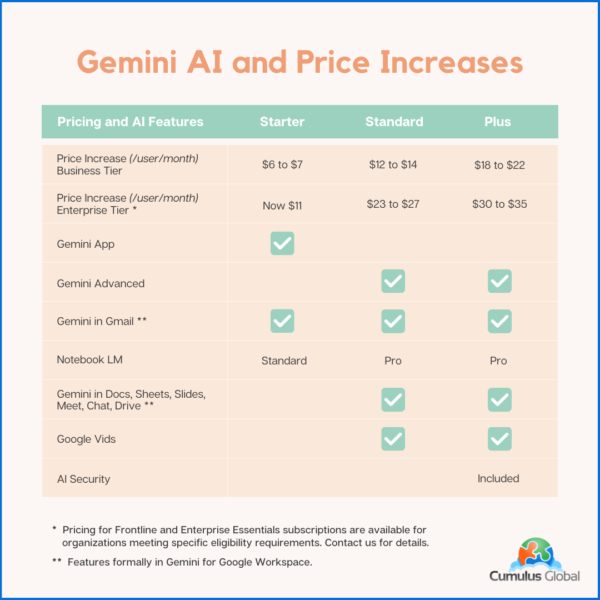
Note that your pricing for Archived Users, Vault, Pooled Storage, Voice, and other products will not change at this time.
Billing Changes
Google has indicated that it will cease billing for Gemini for Google Workspace licenses as of the end of January 2025.
As these services are billed in arrears, expect to see Gemini for Google Workspaces included on February 2025 invoices that cover January 2025.
If you have an existing single or multi-year agreement that includes Google Workspace and Gemini for Google Workspace, expect the Gemini for Google Workspace line item to be removed once service for January 2025 has been invoiced. If you prepaid for the year, you may be eligible for a credit or a refund.
We will update this blog post, and communicate with affected customers as we are able to confirm how these issues will be resolved.
Managing Gemini AI within Google Workspace
Admins with appropriate permissions can manage Gemini AI features. Users have limited ability to control AI options.
Admins
Admins have the following options to control AI settings:
- Manage access to Gemini features in Workspace services (Enterprise editions only at this time)
- Turn access to the Gemini app (gemini.google.com) on or off. (Note: this has no effect on other AI features in Google Workspace services.)
- Turn NotebookLM on or off as an additional service.
- Turn access to Google Vids on or off.
- Control whether users can let Google AI take notes in meetings.
- You can turn Google Workspace smart features on or off.
Users
Users can control the following AI options:
- Smart features in Google products
Cumulus Global clients should contact our Service Team for assistance. If you are self-service with Google direct, or have licensing through another Google partner, schedule a call with one of our Cloud Advisors.
Time Sensitive Opportunities
If you have considered upgrading your Google Workspace subscription to a higher tier, we recommend doing so before March 15, 2025.
- We can upgrade your service with a one-year commitment. You still get the newly embedded Gemini AI features while locking in the current subscription price. We can also explore incentives for multi-year commitments.
If you are on a Flexible Plan, consider moving to an Annual Plan.
- While the Flexible Plan allows your monthly cost to directly reflect the number of active accounts, the vast majority of small businesses save money with an Annual Plan.
- Most businesses do not see the number of account removals needed to overcome the 20% surcharge on top of the price increase.
- Please schedule time with a Cloud Advisor to calculate which plan is best for you and your business.
About the Author
 Allen Falcon is the co-founder and CEO of Cumulus Global. Allen co-founded Cumulus Global in 2006 to offer small businesses enterprise-grade email security and compliance using emerging cloud solutions. He has led the company’s growth into a managed cloud service provider with over 1,000 customers throughout North America. Starting his first business at age 12, Allen is a serial entrepreneur. He has launched strategic IT consulting, software, and service companies. An advocate for small and midsize businesses, Allen served on the board of the former Smaller Business Association of New England, local economic development committees, and industry advisory boards.
Allen Falcon is the co-founder and CEO of Cumulus Global. Allen co-founded Cumulus Global in 2006 to offer small businesses enterprise-grade email security and compliance using emerging cloud solutions. He has led the company’s growth into a managed cloud service provider with over 1,000 customers throughout North America. Starting his first business at age 12, Allen is a serial entrepreneur. He has launched strategic IT consulting, software, and service companies. An advocate for small and midsize businesses, Allen served on the board of the former Smaller Business Association of New England, local economic development committees, and industry advisory boards.

 As we head into the new year, we face an uncertain business landscape. Politics, the economy, and technology advances create new tech-related challenges and opportunities. As you make your plans, be ready for these 3 things in 2025.
As we head into the new year, we face an uncertain business landscape. Politics, the economy, and technology advances create new tech-related challenges and opportunities. As you make your plans, be ready for these 3 things in 2025. Back in January of this year, we announced that Cumulus Global was expanding its sustainability program. To help offset the carbon footprint of our offices and operations, we have strengthened our partnership with
Back in January of this year, we announced that Cumulus Global was expanding its sustainability program. To help offset the carbon footprint of our offices and operations, we have strengthened our partnership with 

 Cyber Security Will Change Companies
Cyber Security Will Change Companies As reported in
As reported in 