Debunking Cyber Insurance Myths

Your business faces an ever-increasing array of cyber threats. Beyond protections, cyber insurance is an essential component of a robust risk management strategy. Therefore, understanding cyber insurance realities is necessary for you to make sound security and business decisions. In this post, we focus on debunking common cyber insurance myths.
1MYTH: Cyber Insurance Policies Offer the Same Level of Protection
In reality, policies vary significantly with respect to coverages and services. Opting for bundled policies generally results in coverage gaps, as most general liability policies treat cyber coverage as an add-on.These gaps leave your businesses vulnerable to liabilities and losses.
Standalone cyber insurance policies, provided by financially strong carriers, offer comprehensive protection tailored to the specific needs of your business. They address unique risks associated with cyber threats given your industry, business size, and other risk factors. Standalone policies also often include coverage of forensics, temporary resources, and other recovery needs. Dedicated coverage helps you respond more effectively to a cyber incident.
2MYTH: Your IT Security Measures Dictate Your Premiums.
While robust security practices can positively impact premiums, broader industry trends and company-specific factors play a more significant role in determining pricing.
Industry-wide loss ratios have a substantial impact on insurance costs. Peer group averages impact premiums as well. Insurers assess the risk profile of businesses within sectors. As insurers issue more policies and analyze claims, insurers refine actuarial, incorporating additional factors and risks.
3MYTH: Cyber Insurance Policies do Not Pay Out
Many businesses hesitate to buy standalone cyber insurance policies out of fear that their policy will not pay out in the event of a claim. Reputable cyber insurers with strong financials rarely deny claims with a valid cause..
Inaccurate, or fraudulent, applications are the most frequent reasons for claim denials or reductions.
Your application must accurately reflect your cyber insurance risk profile. The information you provide on your cyber insurance application should reflect a thorough review process. Cybersecurity tools offer verification of your security profile.
4MYTH: Cyber Insurance is All You Need
Many businesses, including yours, may need additional layers of protection for specific cyber risks. These additional coverages may not be available within a traditional cyberinsurance policy.
Cyber warranties offer additional layers of protection by covering these specific elements of cyber risk. Combining cyber warranties with cyber insurance creates a more comprehensive safety net. This approach bolsters your overall security strategy and ensures appropriate coverage.
5MYTH: Robust Cybersecurity Measures Eliminate the Need for Cyber Insurance
Investing in strong cybersecurity defenses provides crucial protection for your business. No security profile or system, however, will stop every cyber attack, data breach, or data loss incident. Cyber threats continually evolve. Even the most secure systems fall victim to sophisticated attacks.
Cyber insurance serves as your financial safety net. Beyond covering direct financial losses, better policies help you recover from incidents that slip through the cracks of your security measures. These resources include forensics, data recovery, customer relations, legal expenses, and more. Cyber insurance protects you financially if and when a cyber attack gets past your defenses.
6MYTH: Obtaining Cyber Insurance is Complicated and Time-Consuming
The thought of obtaining cyber insurance deters many businesses from seeking the coverage they need. Horror stories of complex applications, surveys, and audits create anxiety and fear of the process.
Unfortunately, this myth can come true. Businesses that apply through general insurance agents and fail to leverage knowledgeable IT resources often run into issues during the underwriting process.
Cumulus Global partners with cyber insurance specialists that offer streamlined application processes and non-committal quotes. Our partners work with more than two dozen carriers, ensuring you have options to choose the policies that meet your business needs and budget. Non-biased policy reviews help you understand your coverages and make informed decisions.
Related Information
Cyber Security Requirements for Cyber Insurance (eBook)
5 Questions for Lower SMB Cyber Insurance Premiums (Coffee & Clouds)
Security CPR (Cloud Burst)
Security CPR Managed Security Services (Service Overview)
Your Next Step
Avoid falling prey to cyber insurance myths. Contact us and let us introduce you to our cyber insurance partners.
We can provide you with a Cyber Insurance Risk Assessment and help you assess your cybersecurity profile.
About the Author
 Bill is a Senior Cloud Advisor responsible for helping small and midsize organizations with cloud forward solutions that meet their business needs, priorities, and budgets. Bill works with executives, leaders, and team members to understand workflows, identify strategic goals and tactical requirements, and design solutions and implementation phases. Having helped over 200 organizations successfully adopt cloud solutions, his expertise and working style ensure a comfortable experience effective change management.
Bill is a Senior Cloud Advisor responsible for helping small and midsize organizations with cloud forward solutions that meet their business needs, priorities, and budgets. Bill works with executives, leaders, and team members to understand workflows, identify strategic goals and tactical requirements, and design solutions and implementation phases. Having helped over 200 organizations successfully adopt cloud solutions, his expertise and working style ensure a comfortable experience effective change management.

 To meet widely varying customer needs, Google offers five core subscription options spread over two tiers. For larger organizations with frontline and deskless information workers, Google offers additional, specialized license options.
To meet widely varying customer needs, Google offers five core subscription options spread over two tiers. For larger organizations with frontline and deskless information workers, Google offers additional, specialized license options. 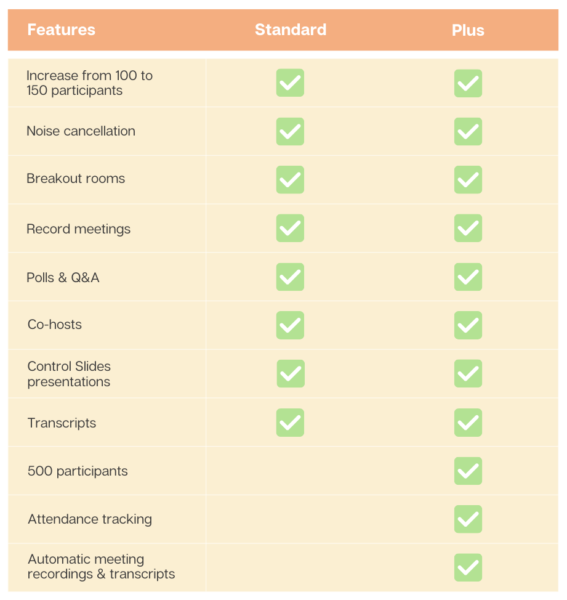
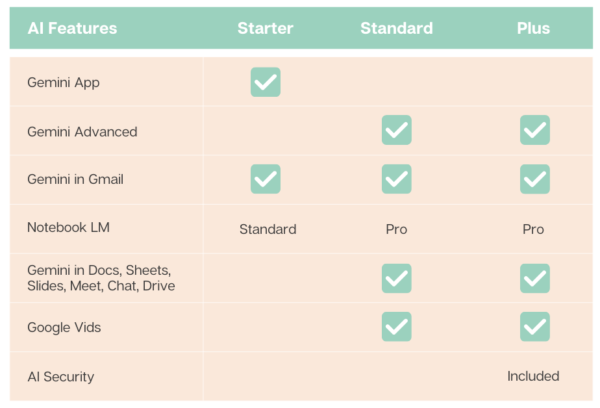
 In today’s fast-paced business world, the ability to maintain continuous PC operations is crucial for your business. With limited resources and manpower, you cannot afford to lose data or prolonged downtime.
In today’s fast-paced business world, the ability to maintain continuous PC operations is crucial for your business. With limited resources and manpower, you cannot afford to lose data or prolonged downtime. 
