Microsoft or Google Calling? Call Your Trusted Advisors
 You work with an IT service provider that learns your business, priorities, and IT needs. They work to address your needs and priorities within your budget and in alignment with your business goals and objectives. When economic conditions shift, the vendors with whom your IT service provider partners – Google, Microsoft, and others – get nervous and begin calling you directly, bypassing your trusted advisors.
You work with an IT service provider that learns your business, priorities, and IT needs. They work to address your needs and priorities within your budget and in alignment with your business goals and objectives. When economic conditions shift, the vendors with whom your IT service provider partners – Google, Microsoft, and others – get nervous and begin calling you directly, bypassing your trusted advisors.
Since February, we have seen and received reports that our customers, and those of other Microsoft partners, are receiving unsolicited calls, emails, and calendar invites from “Microsoft” about their accounts, licensing, and renewals. These unsolicited contacts are NOT Microsoft “solutions consultants” or “international suppliers” as they might claim. They are Microsoft telemarketing contractors tasked with convincing you to upgrade and expand your Microsoft licensing.
Why is This a Problem?
The contractors doing the outreach do not know your business, nor do they know the extent of your relationship with us, or your Microsoft partner.
- Their suggestions are often incorrect.
- They are not aware of how you are using your Microsoft 365 services and the needs of your business.
- They are not aware of other services you are using, such as backup/recovery and third party security services.
- Many of their recommendations will duplicate services and costs.
- The communications and tactics are often aggressive.
- They may state that they have reviewed or audited your account and you need to upgrade. They may also claim that you need to do an audit, giving you the impression that you are out of compliance.
- They may attempt to refer you to specific vendors for assessments and services. These often duplicate services you already have or that can be provided more cost-effectively by us or your current Microsoft partner.
- Customers and Microsoft partners report that the calls and meetings are often just high-pressure sales pitches to buy more seats – a waste of time.
What To Do
If you receive a call or email that you suspect is from a Microsoft “Solutions Consultant” or “International Suppliers”, verify that this is the case. Ask if they are a Microsoft employee or contractor and where they are based. Note that their email address will start with a “v-”, indicating they are a vendor – even though the domain remains “microsoft.com”.
If you do not want to engage, let them know as much and instruct them to contact Cumulus Global, or your partner. We, or your partner, will be happy to screen the call and advise you if the offer is worth considering.
Do you want to engage? Insist that Cumulus Global, or your Microsoft partner, is invited and participates in the meeting. We can provide context to the “consultant” and guidance to you.
Microsoft is not the only vendor that may bypass your IT service provider and contact you directly. It is always best to loop-in your IT service provider.
Your Next Step
At Cumulus Global, our priority is ensuring that you have productive, secure, and affordably managed cloud services. We work to ensure that you do not overspend on services and to focus your IT dollars on the capabilities and services you need.
If your needs or priorities change, let us know or schedule a meeting with a Cloud Advisor. We will help you adapt while keeping your IT services secure and cost-effective.
About the Author
 Bill is a Senior Cloud Advisor responsible for helping small and midsize organizations with cloud forward solutions that meet their business needs, priorities, and budgets. Bill works with executives, leaders, and team members to understand workflows, identify strategic goals and tactical requirements, and design solutions and implementation phases. Having helped over 200 organizations successfully adopt cloud solutions, his expertise and working style ensure a comfortable experience effective change management.
Bill is a Senior Cloud Advisor responsible for helping small and midsize organizations with cloud forward solutions that meet their business needs, priorities, and budgets. Bill works with executives, leaders, and team members to understand workflows, identify strategic goals and tactical requirements, and design solutions and implementation phases. Having helped over 200 organizations successfully adopt cloud solutions, his expertise and working style ensure a comfortable experience effective change management.


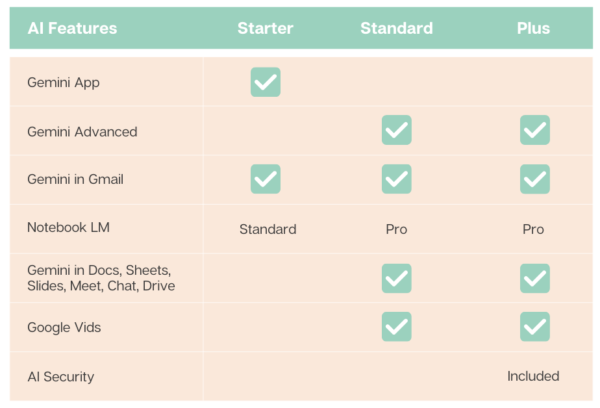
 To meet widely varying customer needs, Google offers five core subscription options spread over two tiers. For larger organizations with frontline and deskless information workers, Google offers additional, specialized license options.
To meet widely varying customer needs, Google offers five core subscription options spread over two tiers. For larger organizations with frontline and deskless information workers, Google offers additional, specialized license options. 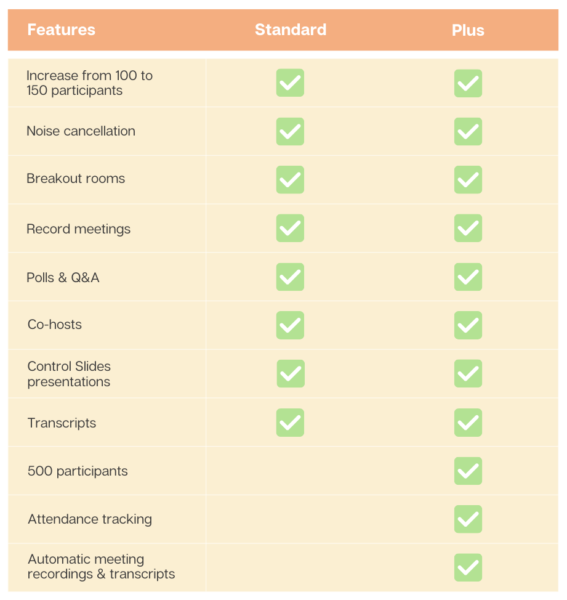

 In today’s fast-paced business world, the ability to maintain continuous PC operations is crucial for your business. With limited resources and manpower, you cannot afford to lose data or prolonged downtime.
In today’s fast-paced business world, the ability to maintain continuous PC operations is crucial for your business. With limited resources and manpower, you cannot afford to lose data or prolonged downtime. 
 Cyber threats are evolving at an alarming rate, posing significant risks to your business. Penetration testing, commonly referred to as “pen testing,” is becoming a vital, proactive tool for assessing your risks.
Cyber threats are evolving at an alarming rate, posing significant risks to your business. Penetration testing, commonly referred to as “pen testing,” is becoming a vital, proactive tool for assessing your risks.
 A common statement we hear from sales experts and consultants is that 60% of IT buyers believe that they have found the solution they need before they contact their first vendor. While we are not sure of the accuracy of this claim, anecdotally we see more small and midsize businesses asking for IT quotes for specific products or services rather than a solution for a need or opportunity.
A common statement we hear from sales experts and consultants is that 60% of IT buyers believe that they have found the solution they need before they contact their first vendor. While we are not sure of the accuracy of this claim, anecdotally we see more small and midsize businesses asking for IT quotes for specific products or services rather than a solution for a need or opportunity. Back in January of this year, we announced that Cumulus Global was expanding its sustainability program. To help offset the carbon footprint of our offices and operations, we have strengthened our partnership with
Back in January of this year, we announced that Cumulus Global was expanding its sustainability program. To help offset the carbon footprint of our offices and operations, we have strengthened our partnership with  Allen Falcon is the co-founder and CEO of Cumulus Global. Allen co-founded Cumulus Global in 2006 to offer small businesses enterprise-grade email security and compliance using emerging cloud solutions. He has led the company’s growth into a managed cloud service provider with over 1,000 customers throughout North America. Starting his first business at age 12, Allen is a serial entrepreneur. He has launched strategic IT consulting, software, and service companies. An advocate for small and midsize businesses, Allen served on the board of the former Smaller Business Association of New England, local economic development committees, and industry advisory boards.
Allen Falcon is the co-founder and CEO of Cumulus Global. Allen co-founded Cumulus Global in 2006 to offer small businesses enterprise-grade email security and compliance using emerging cloud solutions. He has led the company’s growth into a managed cloud service provider with over 1,000 customers throughout North America. Starting his first business at age 12, Allen is a serial entrepreneur. He has launched strategic IT consulting, software, and service companies. An advocate for small and midsize businesses, Allen served on the board of the former Smaller Business Association of New England, local economic development committees, and industry advisory boards.